Introducing tag-based service discovery - Now control what AWS resources get discovered and monitored.
Your AWS service footprint will get larger and larger as you start going through the motions of configuration and testing. Over time, you'll gradually start to see disparate orphaned resources crop up in your AWS account. Tags are a great way to keep track of configured resources and are generally composed of a key and value pair. When used correctly, these simple pairs of strings and special characters can be quite powerful. From aiding in management to helping in searching and sorting, tags perform a number of functions in the AWS management console. Now, you can leverage these same tags in Site24x7 to exclude specific AWS resources and instances from being discovered.
To improve auto discovery, we are bringing in three different modes of tag-based support.
System-generated tags
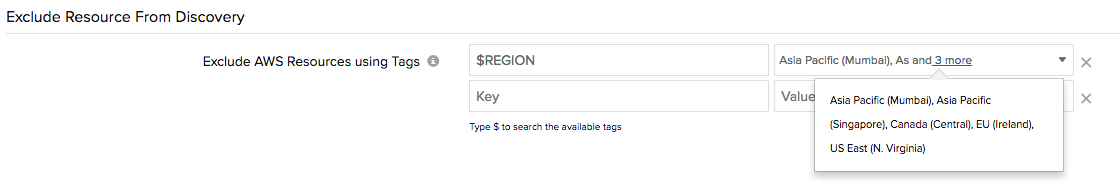
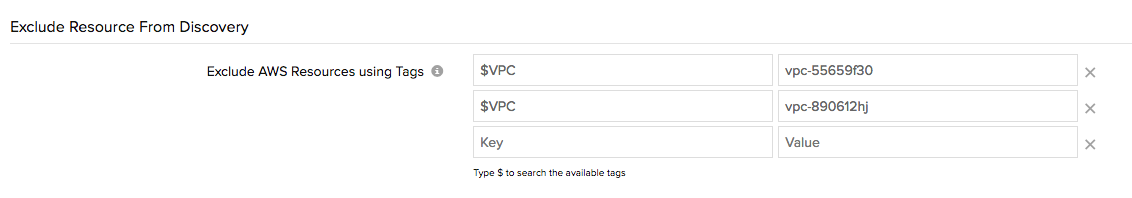
You can use existing resource properties or system attributes to prevent resources from being auto-discovered by Site24x7. Currently, two resource attributes are supported — Region and VPC ID. So any resource attached to a specific region, or instances launched in a particular VPC platform, can be filtered out using this subset. We're also working on adding support for additional unique system attributes related to each AWS service, so look out for even more support for system-generated tags soon.
User-defined tags
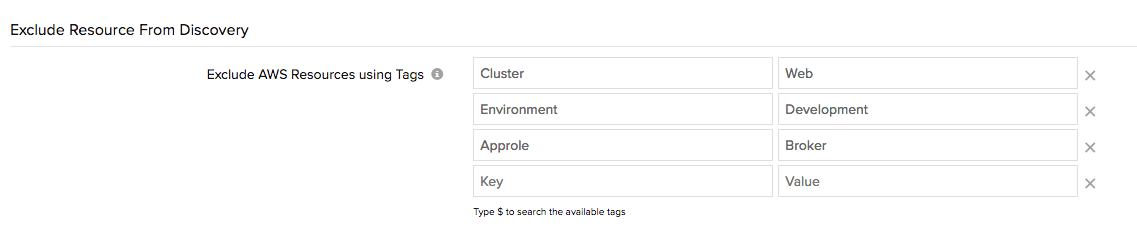
Amazon gives you the power to tag almost anything and everything using the AWS management console. Currently, there are very few limitations in the AWS console when it comes to tagging (the lack of SNS tag support comes to mind), and usually account holders come up with some nifty tagging strategies to manage their resources. The metadata that customers assign to various AWS components are generally called "user-defined tags." With our new support, you can now configure your user-defined tags in Site24x7 and filter the respective resources from discovery.
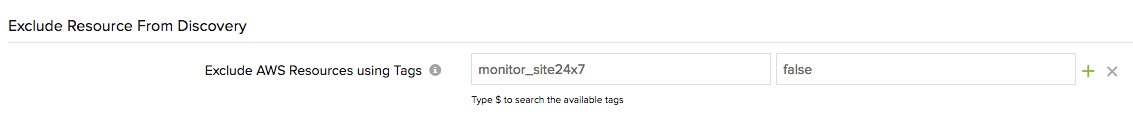
Apply custom tags
If the options above don't really cut it for you, you can assign Site24x7's custom tag to various components in your AWS application environment. All you have to do is tag your AWS resource with the key monitor_site24x7, either individually or in bulk, and set the tags value as "false".
Configure multiple combinations of the above-mentioned labels/tags to be as precise as you want.
How can tag-based auto discovery help you?
More control
By default, Site24x7 automatically discovers all the supported services mentioned in your policy statement, regardless of whether these resources are running in your production or development environment. With tag-based auto discovery, you have a better hold on what gets discovered and what gets monitored.
Makes it easy
Tags simplify discovery so you don't have to:
- Write conditional expressions in your policy statement for a targeted auto discovery.
- Assign multiple service-specific policy templates to narrow down the scope of monitoring.
- Suspend the AWS resource monitor after discovery.
Limit API calls
With the power to filter resources, you get to reduce a little bit of the API overhead that goes towards monitoring your AWS resources.
More enhancements
Along with tag-based support, we are also adding many more enhancements to our AWS infrastructure monitoring capabilities. If you're curious about these new features, we recommend checking out our forum announcement for more information. You can also learn more by visiting our page, detailing our cloud monitoring capabilities.
If you want to try these new enhancements firsthand, log in to your Site24x7 account (sign up if you don't have one?we offer a 30-day, no-strings-attached, free trial) and follow the instructions to connect your AWS account and make full use of our monitoring capabilities.