Join our community of over 13,000 happy customers
What challenges do SOC teams face?
-

Adapting to evolving attacker tactics requires continual security posture adjustments.
-

Overwhelming data volumes impede comprehensive security visibility, hindering proactive threat identification.
-

Complex security tool ecosystems pose obstacles to effective automation.
-

Massive data sets and disparate tools delay root cause analysis (RCA) and troubleshooting, hampering swift incident response to security breaches.
-

Striking a balance between security measures, operational efficiency, and accurate communication to maintain brand reputation and build trust.
SOC teams deal with
How Site24x7 helps SOC teams with securing their IT systems
Protecting website integrity through defacement monitoring
Website defacement poses a significant threat to an organization's reputation, as hackers can insert malicious content, disrupt user experience, or compromise sensitive data.
Site24x7's website defacement monitoring continuously monitors your website for any changes. It uses intelligent logic to identify malicious modifications, alerting SOC teams of potential defacement attempts. This allows for swift action to protect website integrity and reputation.


Securing applications with logs and traces
Modern applications are often complex and interconnected, making them vulnerable to security threats like SQL injection attacks or unauthorized data access.
Site24x7's application performance monitoring along with its log management tool, AppLogs, analyzes logs and traces to provide unmatched security to your applications. They capture details of database queries, API calls, and errors, as well as event logs, syslogs, application logs, and database logs, allowing SOC teams to identify suspicious activity, like unauthorized data access or malicious API calls. By correlating logs with security events, SOC teams can gain a holistic view of potential application security incidents, identify root causes faster, and reduce mean time to repair (MTTR).
Ensuring secure and compliant networks with automated configuration management
Large networks face challenges in maintaining both security and compliance. Unmanaged configurations leave them vulnerable to attacks, while manual audits for compliance are slow and error-prone.
Site24x7's network configuration management (NCM) tool tackles both network security and compliance issues. It automates backups, tracks changes, scans for vulnerabilities, and detects unauthorized modifications, alerting the SOC team for swift action. Additionally, NCM lets you define compliance policies and conducts automated audits, flagging misconfigurations. This empowers SOC teams to enforce secure configurations and ensure compliance with industry standards or internal guidelines.
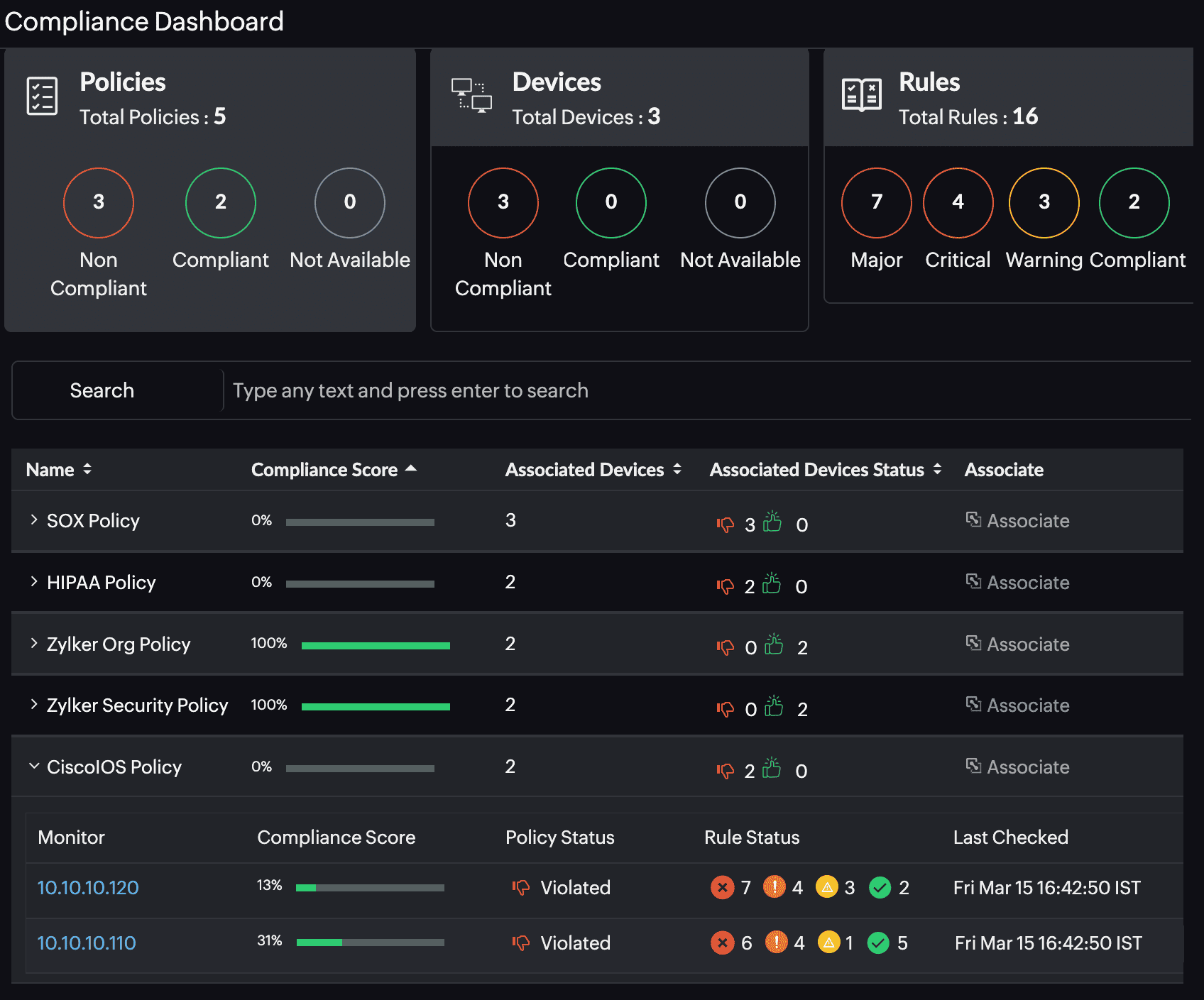

Maintaining compliance with regulatory requirements using logs and guidance reports
Maintaining compliance with industry regulations like the PCI DSS, HIPAA, or the GDPR requires organizations to audit and retain logs for specific periods from diverse systems and applications. Manually managing these while maintaining cloud security best practices is crucial, yet complex and susceptible to error.
Site24x7 AppLogs is a centralized platform for log management of applications, cloud services, and network devices. It ensures secure storage with access controls, adheres to retention policies, and provides search tools and dashboards for compliance audits. Additionally, Site24x7 provides compliance checks for the best practice recommendations provided in the AWS Guidance Report to identify potential security misconfigurations and compliance risks within your AWS environment.
Securing critical system files with server resource checks
Ensuring the integrity of critical system files on servers is crucial for system stability and security. Unauthorized modifications or malware attacks can corrupt these files, leading to malfunctions, data breaches, or even complete system outages—yet monitoring manually is tedious and unreliable.
Site24x7's server resource checks secure critical system files by monitoring specific files or directories on your servers. Any changes to the monitored files, such as modifications to content, permissions, or ownership, trigger immediate alerts for the SOC team. This allows for swift investigation and remediation, minimizing the impact of potential security incidents.

Why is ManageEngine Site24x7 the best fit?
-

Longevity: As a division of Zoho, ManageEngine promises a long-term commitment and profound R&D.
-

Synergy: Site24x7 is part of ManageEngine's IT management suite, which provides holistic solutions.
-

Security: Privacy, compliance, and security are the three mantras at every layer of Site24x7.
-

Scalability: Over 13,000 customers trust Site24x7 to monitor their growing IT infrastructures.
Start your journey
What made us go with Site24x7 was the fact it was all-encompassing. It was able to monitor not just infrastructure but also services.
