Email Security
Based on the authentication framework used, email-security-related assertions are multiple types.
Sender Policy Framework (SPF)
SPF is an email authentication protocol that helps protect your domain against phishing attacks. It specifies which mail server is authorized to send emails from your domain and prevents your emails from getting marked as spam by receiving servers.
SPF record consists of individual units called terms, which are further classified into mechanisms (all/include/a/mx/ptr/ip4/ip6/exists) and modifiers (redirect and explanation).
v=spf1 include:_spf.example.com ~all
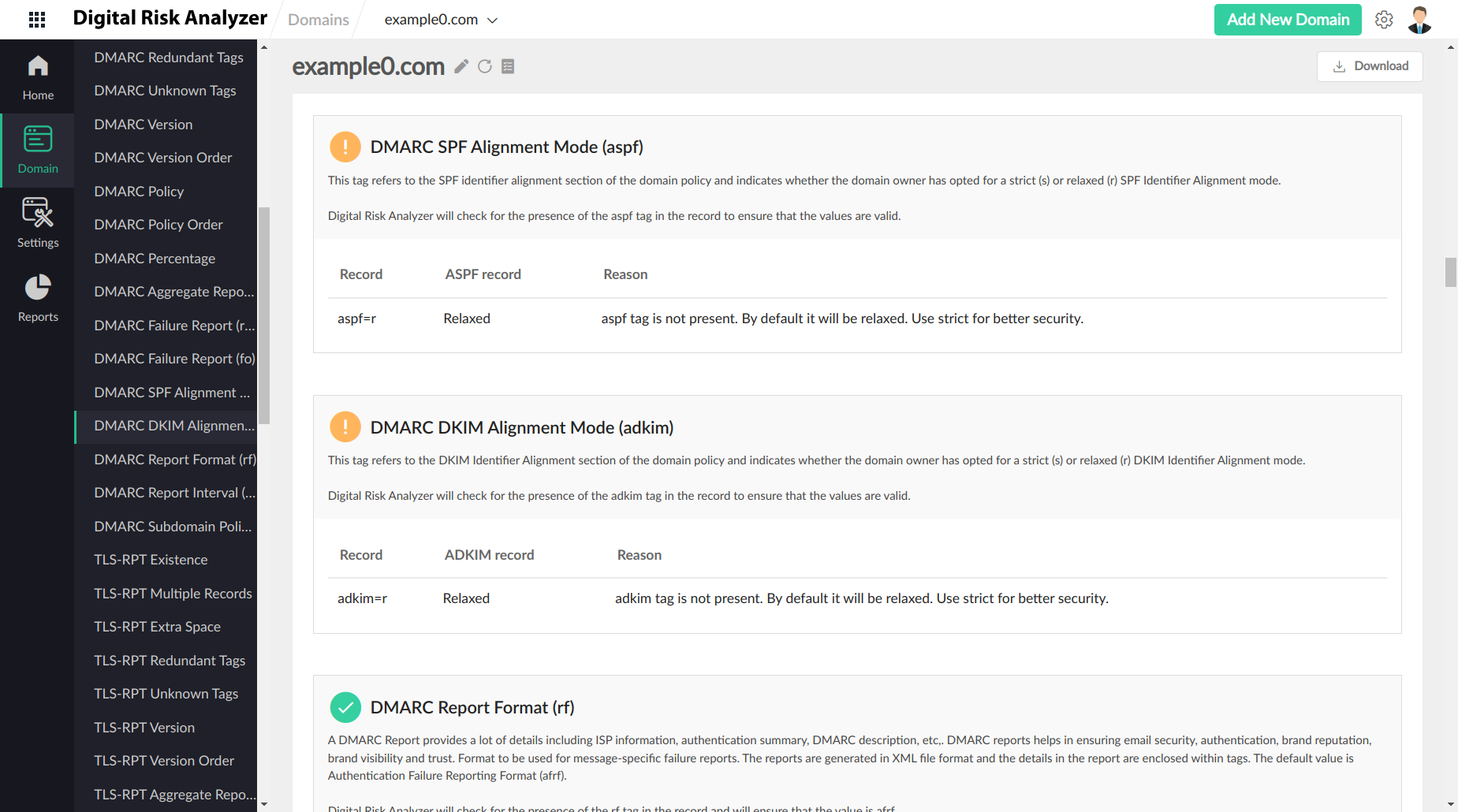
Domain-based Message Authentication Reporting and Conformance (DMARC)
DMARC is an open email authentication system that protects email senders and recipients from spam, spoofing, and phishing attacks. DMARC allows the domain owner to publish a DMARC policy addressing the receivers, stating what to do if its email authentication fails. SPF and DomainKeys Identified Mail (DKIM) standards are used for email authentication.
v=DMARC1; p=quarantine; rua=mailto:dmarc-feedback@example.com,mailto:tld-test@thirdparty.example.net; pct=25
|
Tag |
Symbol |
Required |
Possible Values |
|
Version |
v |
✓ |
DMARC1 |
|
Policy |
p |
✓ |
none | quarantine | reject |
|
Percentage |
pct |
0-100 100 (default) |
|
|
Reporting URI(s) for aggregate data |
rua |
email address comma-separated |
|
|
Reporting URI(s) for Failure data |
ruf |
email address comma-separated |
|
|
Failure Reporting Options |
fo |
both - 0 (default) any - 1 dkim - d spf -s |
|
|
SPF alignment |
aspf |
strict - s relaxed - r (default) |
|
|
ADKIM alignment |
adkim |
strict - s relaxed - r (default) |
|
|
Report Format |
rf |
afrF (Authentication Failure Reporting Format) (default) |
|
|
Report Interval |
ri |
>0 (no of seconds) 86400 (default) |
|
|
Subdomain Policy |
sp |
none | quarantine | reject |
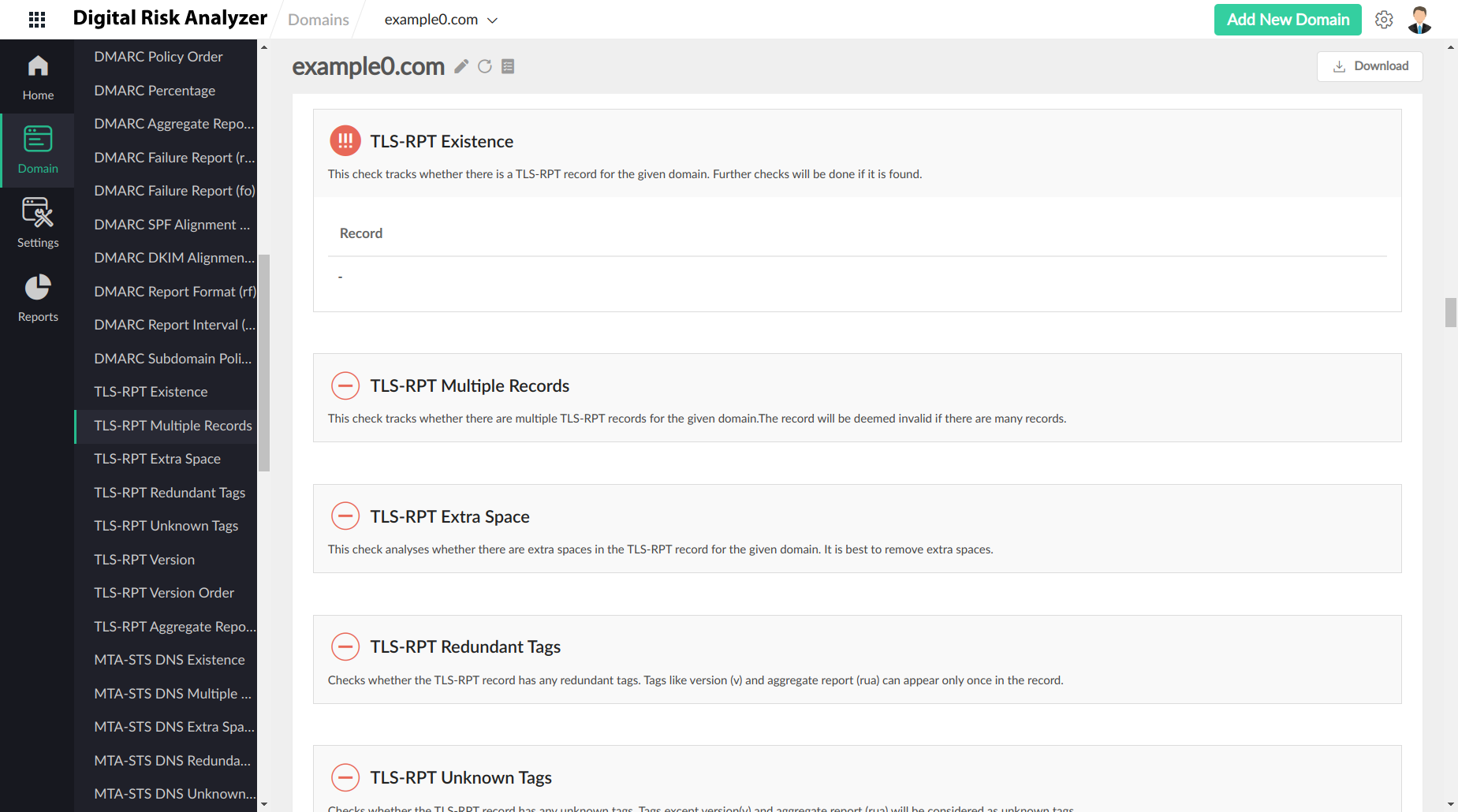
SMTP TLS Reporting
SMTP TLS Reporting is a reporting mechanism that allows to send reports on possible security issues that servers experience while connecting to inbound email systems.
As SMTP protocol has an open architecture, the connections between SMTP servers are prone to SMTP TLS downgrade attacks. With SMTP TLS reports, users can get detailed insights and start enforcing TLS connection security via additional security standards like DNS-Based Authentication of Named Entities (DANE) and Mail Transfer Agent Strict Transport Security (MTA-STS).
v=TLSRPTv1;rua=mailto:reports@example.com
|
Tag |
Symbol | Required | Possible values |
|
Version |
version |
✓ |
TLSRPTv1 |
| Reporting URI(s) for aggregate data |
rua |
✓ |
email address |
MTA STS DNS Existence
SMTP MTA Strict Transport Security (MTA-STS) is a mechanism enabling mail service providers (SPs) to declare their ability to receive Transport Layer Security (TLS) secure SMTP connections and to specify whether sending SMTP servers should refuse to deliver to MX hosts that do not offer TLS with a trusted server certificate. MTA STS happens via a combination of DNS and HTTPS.
DNS
v=STSv1; id=20160831085700Z;
| Tag | Symbol | Required | Possible values |
| Version | v | ✓ | STSv1 |
| id | id | ✓ | 1*32 (ALPHA / DIGIT) |
HTTPS
mode: testing
mx: mx1.example.com
mx: mx2.example.com
mx: mx.backup-example.com
max_age: 1296000
| Tag | Symbol | Required | Possible values |
|
Version |
version |
✓ |
STSv1 |
| Mode | mode |
✓ |
enforce |
|
MX |
mx |
✓ |
mx: mail.example.com |
| Max age |
max_age |
✓ |
<= 31557600 |
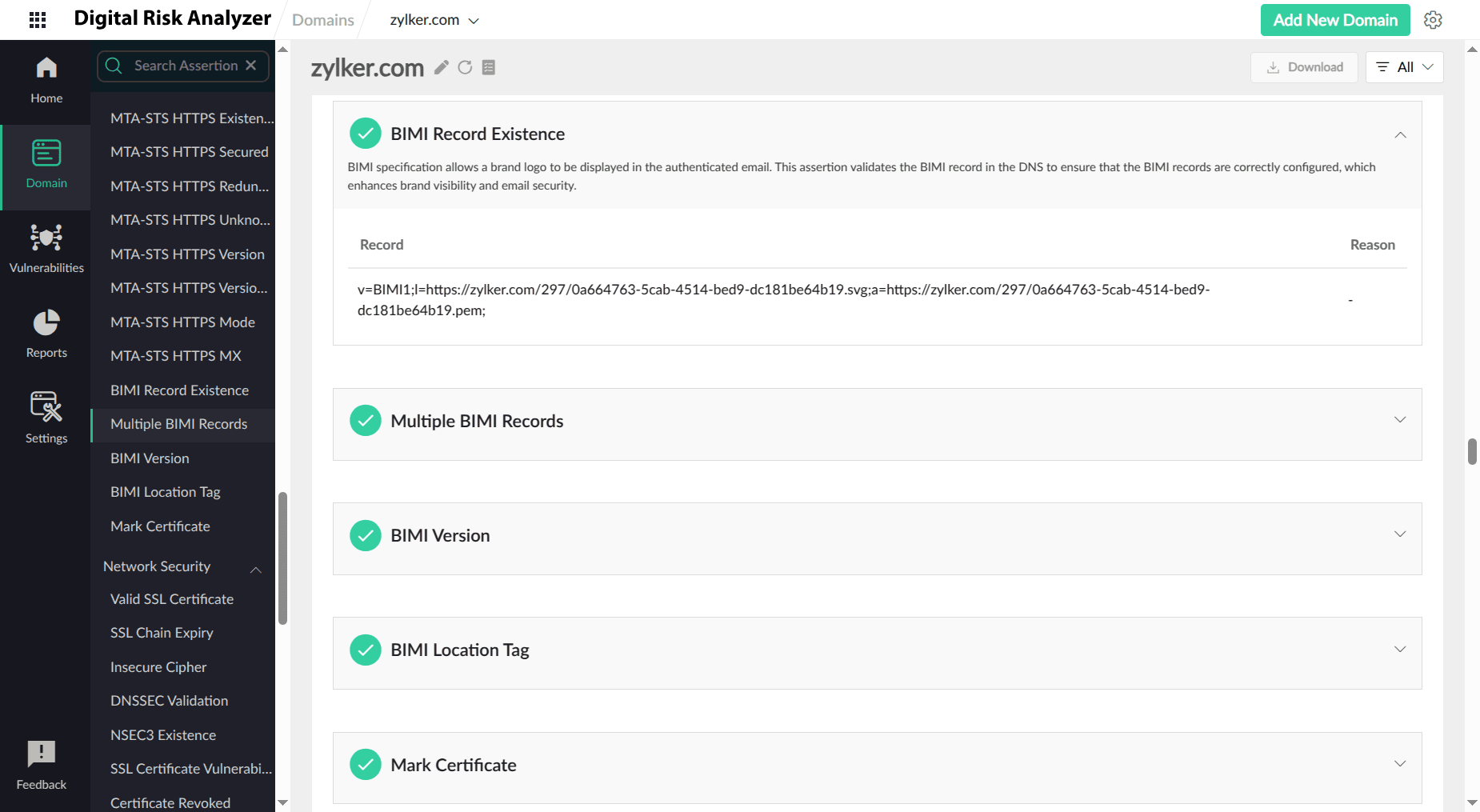
BIMI
Brand Indicators for Message Identification (BIMI) is an email authentication standard that allows organizations to display a registered logo next to authenticated emails. This specification builds trust and brand recognition, making it easier for recipients to identify legitimate emails and avoid phishing attempts. However, implementing BIMI can be a complex process, requiring robust email authentication, i.e., DMARC, and a verified trademark.
Digital Risk Analyzer helps prevent BIMI vulnerabilities by thoroughly assessing your email authentication configuration and identifying any weaknesses. It checks your DMARC, SPF, and DKIM records for proper setup and alignment, ensuring that your domain is protected against spoofing and unauthorized use. By proactively identifying and addressing these potential vulnerabilities, Digital Risk Analyzer helps you implement BIMI securely and effectively, maximizing its benefits while minimizing risks.