AWS Monitoring helps you gain observability into your AWS environment
AWS best practices: S3 security
Amazon S3 is an incredibly flexible cloud storage solution offered by Amazon Web Services (AWS). However, securing the S3 buckets requires a deep understanding of the different security layers and the best practices available. Read along to learn the AWS S3 security checklist to fortify your AWS infrastructure.
Amazon Simple Storage Service (Amazon S3) has been the pioneering service that provides unlimited cloud storage at a low cost. Unfortunately, Amazon S3 has been the subject of discussion for some of the largest data breaches in recent history.
When S3 buckets are left publicly accessible, the resulting data loss can be costly. Capital One was fined a whopping $80 million for the 2019 hack of 100 million credit card applications, and until then, no one had realized how expensive a missing wildcard(*) could be. Yet another leak of the personal information of up to 350,000 users at SSL247 paints an image of the cloud itself as a risk offering minimum viable compliance or security.
So, what are the security recommendations available for users to access S3? Let's find out.
Best practices to secure S3 buckets
For companies of all sizes, security practices preventing data leaks and accelerating incident response are vital. When multiple directories and files of varying formats are all stashed away together in S3, it becomes all too easy for something to be mistakenly put among them and left unnoticed.
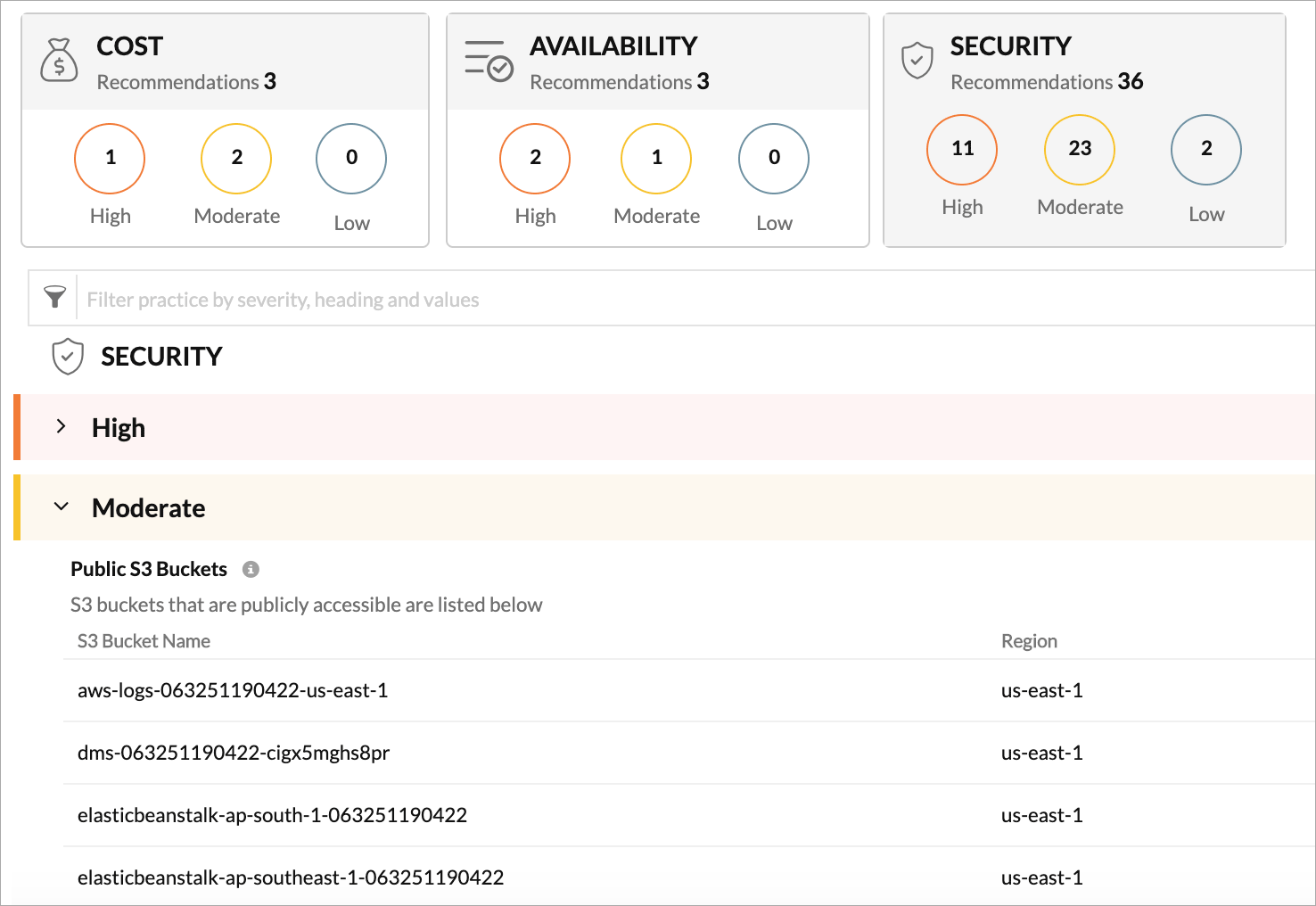
With AWS monitoring, you gain access to AWS guidance reports, which can be used as a personal cloud consultant. Guidance reports examine the configuration and resource utilization of AWS services to offer the best practice recommendations in three different categories: Cost, Availability, and Security.
AWS S3 security checklist
-
1. Restrict publicly accessible S3 buckets
When S3 buckets are accessible publicly, anyone across the globe can read the bucket by listing the objects stored, or upload and remove objects without any oversight. This can lead to surprises on your AWS bill, since each API is chargeable.
With an efficient monitoring tool, you can check the buckets and user policies (except the access control lists) of the monitored S3 buckets, which provides the list of publicly accessible buckets. With this information, you can decide if the bucket in question requires public access. If not, restrict access.
-
2. Enable encryption of buckets
It is essential to encrypt the S3 data at the bucket level instead of the object level to protect the S3 buckets from attackers or unauthorized personnel. With Amazon S3, Server Side Encryption (SSE-S3 or SSE-KMS) applied to an empty bucket guarantees that the data uploaded to the bucket in the future is encrypted (though this does not encrypt any data already stored in the bucket).
Monitor your S3 ecosystem to identify the buckets where the S3 bucket encryption is disabled so that you can make informed decisions about whether to encrypt the data at the bucket level or not.
-
3. Enable server access logging
Logging predominantly helps in root cause analysis following incidents. When server access logging is enabled on a bucket, it captures the details of requests (PUT, GET, and DELETE) that are made to that bucket and its objects. However, by default, Amazon S3 does not collect the server access logs.
Identify the S3 buckets where the server access logging is disabled using an AWS monitoring solution. For any data breach investigation, S3 access logs can track data access patterns over your buckets.
-
4. Enable MFA delete in S3 configuration
MFA delete is a bucket-wide policy that adds an extra layer of security by protecting the deletion of the versioning files, i.e. it deletes the file from the bucket but keeps a version that can't be deleted. If you have only permanent data in the bucket (not temporary or staging data), MFA delete is the option for you.
Ensure that the AWS monitoring tool reports you with information on which buckets have disabled MFA delete so that you can make informed choices about enabling or disabling the MFA delete option.
Security standards complying with best practices
Organizations across the globe have multiple security standards for cloud security and compliance that they need to comply with. By complying with these security standards, you can ensure that your AWS cloud instances follow the major protocols like protecting the system with firewalls, configuring the passwords and settings, protecting stored cardholder data, and more.
The above four security best practices listed will cover the following standards for Amazon S3:
- Payment Card Industry Data Security Standard (PCI DSS)
- General Data Protection Regulation (GDPR)
- National Institute of Standards and Technology (NIST)
- Australian Prudential Regulation Authority (APRA)
- Monetary Authority of Singapore (MAS)
Additionally, best practices two and three will cover the Health Insurance Portability and Accountability Act (HIPAA). Ensure your AWS S3 adheres to the list of security and compliance standards for public clouds using these four best practices.
Why Amazon S3 monitoring?
Measures to prevent impending threats are important, but it is difficult to prevent every threat. This is where a proactive monitoring solution comes into play to close the gaps. With Amazon S3 monitoring, you can monitor the operations on your objects and buckets by tracking the HTTP requests for individual CRUD (create, read, update, and delete) operations or all the requests made to the objects in a S3 bucket. Furthermore, keeping a close eye on the bucket size and the object count helps you track the storage usage and capacity growth.
In security terms, the above-mentioned data breaches occurred due to a security misconfiguration—in simple terms, the front door was left wide open for hackers. Even though AWS handles the security of the cloud, each user is responsible for the security of data in the cloud. With numerous AWS S3 security vulnerabilities, it's recommended you leverage a strong AI-powered AWS monitoring tool that has a built-in best practice check.